Elevate your services with built-in security
Industrial cybersecurity that protects operations, empowers safety, and ensures business continuity.
If you’re delivering complex industrial systems and services to critical infrastructure clients, cybersecurity isn’t just a back-office function – it’s a competitive differentiator. The customers are asking tougher questions, regulators are tightening expectations, and any incident – even one on a client site – can quickly cascade back to you.
The challenge is protecting highly customized environments, often built with legacy stacks, while still ensuring remote access, long-term maintainability, and tight delivery schedules. That’s where things get tricky.
- Meeting increasing OT security expectations in tenders
- Supporting diverse client environments securely
- Avoiding risk when providing remote access or system maintenance
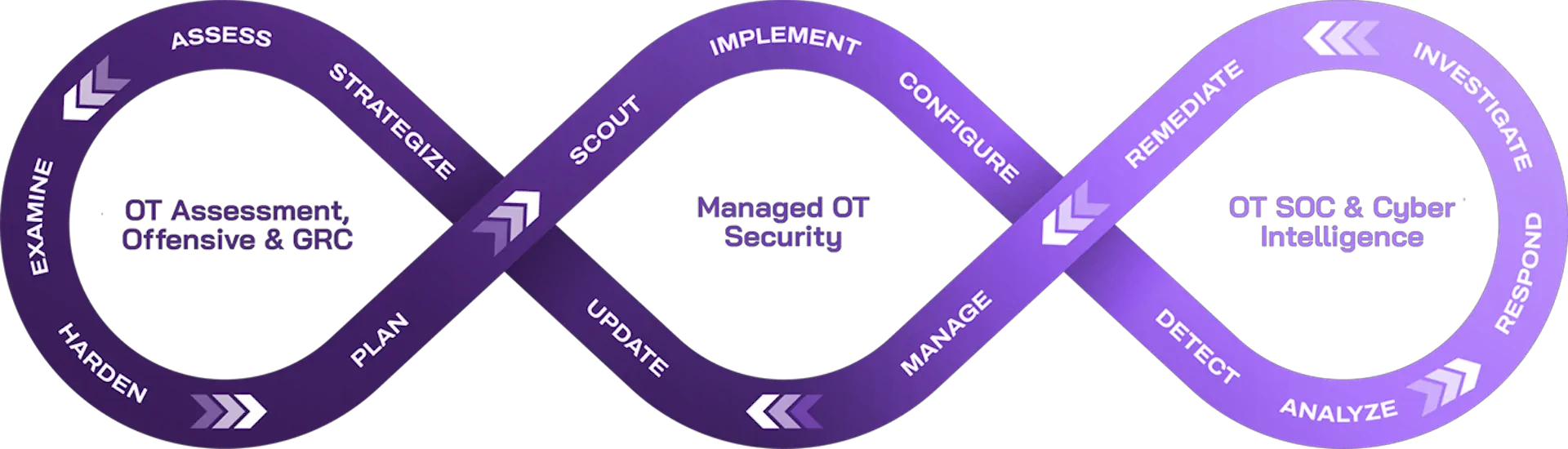
OT Cybersecurity Evaluation
#Network_Posture_Mapping #Security_Assessment #OT_Cyber_Risk_Evaluation #Mitigation_Implementation
You can’t secure what you haven’t mapped. Before deploying or maintaining any client system, you need a clear view of the network structure, the gaps against security frameworks, and the real risk exposure.
These evaluations help you avoid surprises during delivery and ensure your solutions are hardened from the ground up.
Adversary Services
#Penetration_Testing #Reverse_Engineering #SAST_DAST #Attack_Simulation
Clients expect you to deliver secure systems – and increasingly, to prove it. Pen tests, attack simulations, and code reviews aren’t just about security anymore – they’re becoming part of procurement.
These services help you validate your offer, avoid future liability, and demonstrate maturity during tenders.
Incident Response
#Incident_Response_Readiness #Compromise_Assessment
Even if the attack happens on the client side, your name might still be on the system. Having an incident response plan and being able to assess potential compromise shows clients you’re not just delivering a product – you’re standing behind it.
It also helps you manage reputational risk across shared environments.
Consulting / GRC
#OT_VCISO #OT_Tender_Support #OT_Security_Requirements_Definition #Crisis_Management
Clients often lean on you for guidance – especially smaller utilities or operators. Offering OT Virtual CISO capabilities or helping respond to tender requirements elevates your value from vendor to trusted partner.
It also helps you align your practices with what’s being asked at the global compliance level.
OT Security Training
#OT_Fundamentals #OT_Advanced #Secure_PLC_Coding #Other_Training
Your teams are often the ones configuring, commissioning, or even troubleshooting post-go-live. Giving them strong OT security training – especially in secure coding or protocol handling – reduces risk during deployment and supports safer long-term operations for your clients.
Managed OT Security
#Digital_Twin #Whitelist #EPP #Network_Sensors #IPS_IDS #Safe_USB #One_Way_Diode #Remote_Access #ZTNA #IoT #PAM #OT_Vulnerability_Management
Whether you’re integrating USB protections, ZTNA platforms, or passive monitoring, these tools are key to packaging security into your services.
They also help you meet baseline expectations in RFPs and give your field teams better control over what’s running on-site.
Cyber Threat Intelligence
#OT_CTI
You need to know which threats are trending in your clients’ regions and verticals – not just globally. CTI lets you tailor your security controls to real attacker behavior and back up your recommendations with hard evidence.
It also strengthens your position during incident post-mortems or pre-sales risk discussions.
OT Security Operations Center
#OT_SOC
Clients increasingly expect monitoring – especially in high-criticality environments. Having OT SOC capabilities, or at least the ability to plug into one, shows that your offering doesn’t stop at delivery.
It also helps detect potential issues before they escalate into service-level disputes.
Why Y Cyber
Strengthen your offer with validated, field-tested OT security services
Operate through flexible engagement models – from co-delivery to white-labeling
Built specifically for integrators, EPCs, and engineering teams working in complex industrial environments
Help your clients meet security demands while increasing your own value in regulated, high-stakes markets