Industrial operations protected at every level
Industrial cybersecurity that protects operations, empowers safety, and ensures business continuity.
Operating industrial environments today means contending not only with a growing wave of cyber threats – but also with mounting regulatory demands. From ransomware attacks to strict new frameworks like NIS2, the Cyber Resilience Act (CRA), and the New Machinery Regulation (NRM), asset owners are expected to secure both operations and compliance.
The real challenge is staying resilient and competitive while ensuring uptime, managing complex supply chains, and modernizing legacy infrastructure. With Y Cyber, you can stay aligned with evolving global and local standards – without compromising performance.
- Protecting OT infrastructure from modern cyber threats
- Ensuring compliance with NIS2, NRM, CRA, and other regulatory frameworks
- Avoiding costly downtime from ransomware or sabotage
OT Cybersecurity Evaluation
#Network_Posture_Mapping #Security_Assessment #OT_Cyber_Risk_Evaluation #Mitigation_Implementation
Before you make decisions, you need visibility. These services help you map your network, assess risk, and compare your current posture against industry standards like IEC 62443.
From there, you’ll get a clear list of priorities – practical, OT-specific actions you can take to reduce risk and harden your operations.
Adversary Services
#Attack_Surface_Discovery #Penetration_Testing #Red_Teaming #Attack_Simulation
Once your foundation is set, it’s time to test it. These offerings simulate real-world attacks – from red teaming to phishing and physical intrusion – so you can uncover vulnerabilities in both your systems and your processes.
They show you what an attacker would find first, and how ready your team really is to respond.
Incident Response
#Incident_Response_Readiness #Compromise Assessment
When something goes wrong, you need to be ready. These services help you prepare for and respond to incidents through maturity assessments, incident response planning, compromise checks, crisis simulations, and continuous improvement.
You’ll gain confidence knowing that if a breach occurs, your team knows how to act – and you’ll have Y Cyber specialists on hand, backed by defined SLAs, to support your response and help contain the damage.
Consulting / GRC
#OT_Security_Requirements_Definition #OT_Virtual_CISO #Crisis_Management
To build a strong, defensible OT security program, you need structure and alignment. These services help you define policies, set clear roles, and align suppliers.
With an OT Virtual CISO or expert guidance, you gain direction, credibility, and the ability to speak security in business terms. And through tabletop exercises, your leadership team learns how to react confidently when real-world pressure hits.
OT Security Training
#OT_Fundamentals #OT_Advanced #Secure_PLC_Coding #Other_Training
Tools don’t secure themselves – people do. These trainings help your engineers, technicians, and operators understand OT-specific threats, apply secure coding practices, and stay aligned with evolving standards. Whether you’re onboarding new talent or sharpening veteran skills, this is how you build a culture of security across your plant.
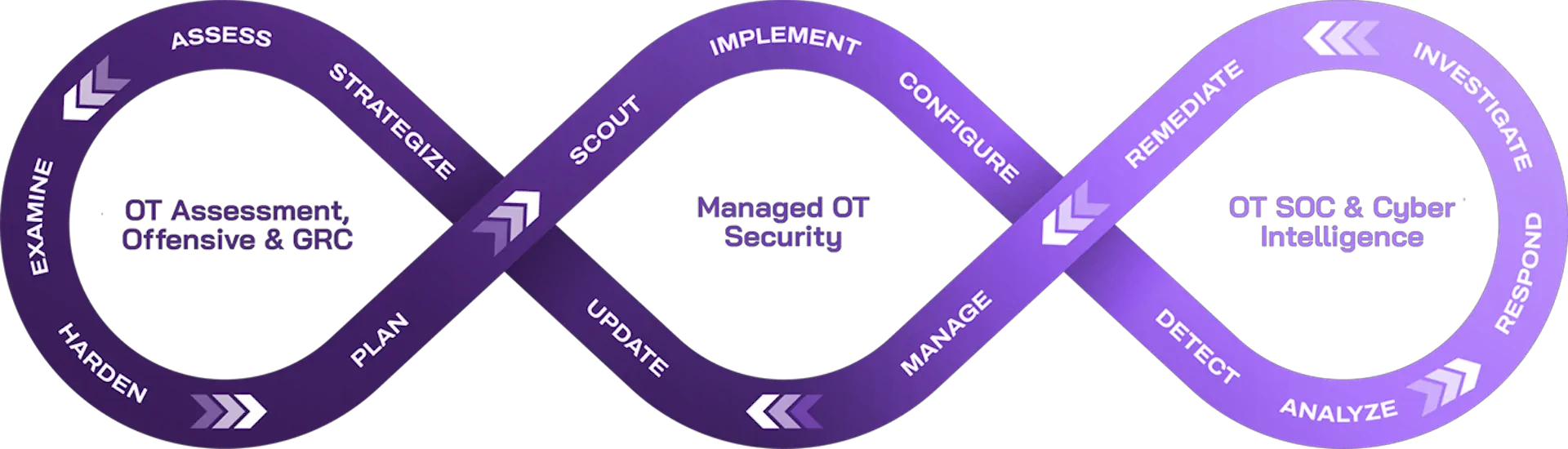
Managed OT Security
#Digital_Twin #Whitelist #EPP #Network_Sensors #IPS_IDS #Safe_USB #One_Way_Diode #Remote_Access #ZTNA #IoT #PAM #OT_Vulnerability_Management
You can’t defend what you don’t control – and this is where the specialized OT Security solutions come in. They help you build a secure operational baseline with real-world constraints in mind: legacy systems, fragmented networks, and minimal downtime windows.
Whether it’s a digital twin to safely test impact, USB protection, remote access security, or IoT access management, these solutions give you hands-on, scalable ways to lock down your environment without slowing production. The best part? Most of them can be phased in gradually, aligned with your maintenance cycles.
Cyber Threat Intelligence
#OT_CTI
You need to know who’s out there and what they’re targeting – especially in your geography or industry. OT CTI gives you that visibility. It filters out the noise and focuses on campaigns, malware families, and actor behaviors that are actually relevant to your plant’s technology stack and exposure.
When something happens in your region or sector, you want to know before it hits your perimeter – that’s what CTI gives you: foresight.
OT Security Operations Center
#OT_SOC
Monitoring industrial networks is not the same as monitoring IT. With an OT-dedicated SOC, you get experts who understand your PLCs, SCADA traffic, and production line rhythms – not just Windows logs.
You get alerts that matter, not a flood of irrelevant tickets. If you’re serious about proactive detection and timely response, then this is what ties everything together: eyes on glass, backed by security experts who understand your plant.
Why Y Cyber
Deep OT-specific expertise, from field-level protocols to plant-wide architectures
Full alignment with international standards like IEC 62443 and NIS2
Modular, scalable services tailored to your operational and business lifecycle
Rapid deployment with proven references across critical infrastructure and industry